CryptoPHP: A new threat for CMS
My website has recently been compromised by a trojan known as CryptoPHP. I am writing this article as soon as I clean up my server to urge other webmasters to take action against this sneaky trojan.
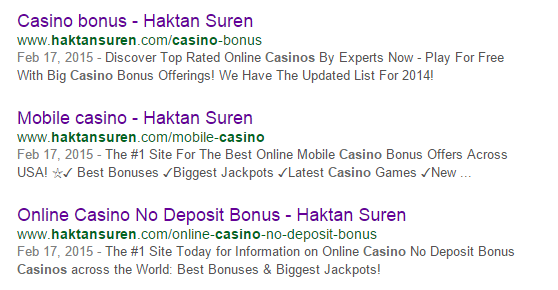
Today, I have got an email from my brother about some pages created that are not belong to my website. They are mostly related with the “casino” keywords and I realized that those pages actually made into Google search index.
After a quick inspection (by mostly disabling plugins one by one). I found the root cause of the problem. I have realized a small PHP code inserted at the bottom of the plugins and theme index page that looks like.
if (!defined('WP_OPTION_KEY')) {
include_once 'social.png';
}
I checked the current directory and saw the social.png file. I think the name social.png is a very smart choice for a trojan. Nobody suspects anything without the symptoms. And It is definitely a better cover name than random characters/numbers (I know I sound like giving credit to the hacker but that’s true).
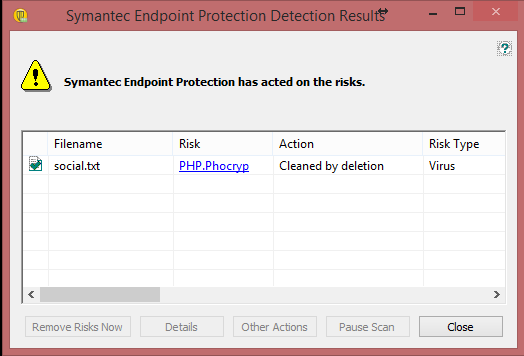
When I try to download the PNG file, Symantec alerted me for a trojan called “PHP.Phocryp” and quarantined the file immediately. Although Symantec classifies this trojan as “Low Risk” (probably because it does not harm the computers), my hunch suggest otherwise and I decided to do more research.
Based on my search, I found that the trojan was first released in Nov 2014 and effecting a few thousands websites especially content management systems like Drupal, WordPress and Joomla. It has been reported that it can control the server communication, email communication as well as manual control by using the built-in functions of the CMS.
I was able to extract the code from the PNG file to do further analysis (You can find the full code here http://pastebin.com/9EnGW7ib). First thing I realized, it was creating some pages on my website to provide traffic to client websites listed below illegally (a.k.a. Blackhat SEO).
pailywarn.com evexampe.com sholise.com arditat.com factiod.com lessied.com sultmel.com callmenauw.net blackmorgana.com stranges.info huntergil.biz milkaxe.biz ramakit.biz quoteboll.biz singletwo.net vivalites.biz cooperdup.mx hantersid.biz qitiwolf.org domesistance.com easibilitary.com kittsburg.com uganonym.com austeal.com divisits.com hortwava.com mountil.com pointern.com trailmorey.com worldcut.biz tablemaster.in joncon.in frogprogs.biz chinesemaster.biz pic2takes.biz goodoo.biz fmdon.pw ignew.in etymologi.in stonerock.in fmfoo.in
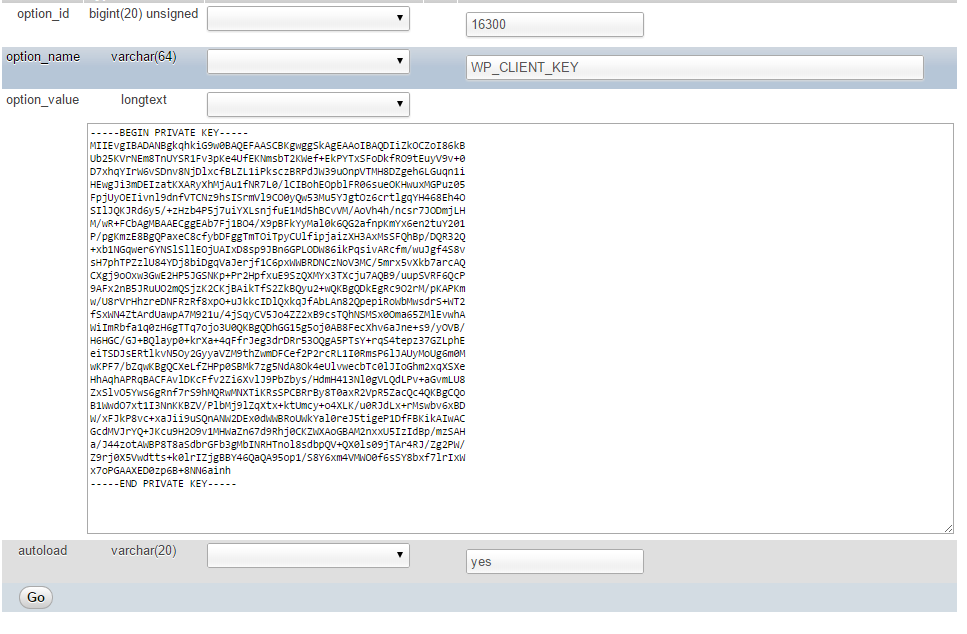
It also created a hidden admin account which I think allow the hacker to log into the admin section any time he wants.
To fix this issue, I have made a ‘grep’ search on the server and removed all the social.png files and the codes that trigger. And then I removed the fake admin account and the entries in the databases especially in wp_options table.
There is a whitepaper published about this vulnerability as soon as the trojan had struck its first victim in Nov by Foxit Security. You can take a look at the details here
Please leave a comment at the bottom, if you are the victim of the trojan CryptoPHP and share your experience about how you inspected and eradicated the problem.

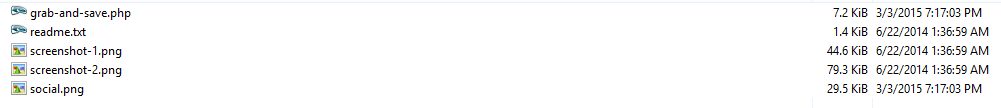





Wrap your code in
<code class="{language}"></code>tags to embed!